Email spoofing: Definition and how spoofing works

What is a spoofing email?
We’re glad you asked! Today we’ll explain:- What email spoofing means
- How email address spoofing works
- How to spot email spoofing
- How to prevent email spoofing
- How to tell if someone is spoofing your email
- What to do if your email address has been spoofed
- Different types of spoofing
Email spoofing definition
In email spoofing, like other forms of spoofing attacks, cybercriminals try to scam recipients by faking an identity. They falsify the sender email address, name and/or IP address so the message appears trustworthy. Usually, the spoofed email has the sender name of a friend, family member, or well-known business.A spoofed email is often used to spread malware or steal personal data. For example, the spoofed message may include phishing links that take you to a pharming website designed to trick you into entering sensitive information. Or the email will contain file attachments that seem harmless at first glance. However, if downloaded, the file contains viruses that give the hacker access to all kinds of data on the device.
How does email spoofing work?
In a spoofing attack, the spoof email sender’s address looks identical to a genuine, trusted email address.To understand how email spoofing works, it’s important to know that an email consists of several parts:
- the body of the email
- the header, which includes the sender’s name and email address
- the “envelope”, which is the technical information that tells the receiving server who the email sender and recipient are.
Instead, domain owners and email service providers have to utilize authentication processes such as DMARC (Domain-based Message Authentication, Reporting, and Conformance), SPF (Sender Policy Framework), and DKIM (Domain Keys Identified Mail) to verify an email’s sender information. If these authentication processes are not in place, emails from falsified senders can bypass spam filters and land right in the recipient’s inbox.
How can I check email for spoofing?
The sender information you receive in an email can clue you in to whether its sender address is legitimate. But it’s not contained in the header you see at the top of the email message listing the sender, subject and date, but in what’s known as the “extended header” or “full header”.When logged into your mail.com account in a web browser, you can click on the lowercase i that appears in the upper right corner of the message (next to the date) to view the extended email header:
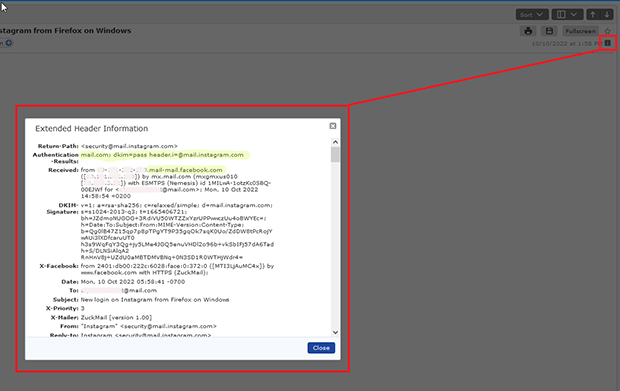
To check an email for spoofing, you can go to the extended header and:
- Look under Received to make sure the email server that originally handled the email matches the displayed Sender. For example, if you see “Sender: Service@BankofAmerica.com” but “Received: from spammer.mcspam.com (23.364.454.44)“, you are dealing with a spoofed email.
- Look under the Authentication-Results to see whether the email has been authenticated by SPF, DMARC, and/or DKIM. Check for a “pass” or “fail” result, which will look something like “(spf-fail)” or “dkim=pass”. A “fail” could be an indication of a spoofed email.
- Look under Return-Path to see the email address where any replies to the email would be sent. A return-path email domain that does not match the domain of the From: address can be a sign of spoofing.
How can I protect myself against email spoofing?
For an email recipient, spoofing is only dangerous if the fake sender actually manages to trick you into giving them money, revealing sensitive data, or installing harmful programs. So, the best protection against spoofing emails is learning to recognize and avoid common email scams:
- Look for signs of spam and scams such as misspelled sender addresses and subject lines or strangely worded messages.
- Do not click on any links in emails in emails without checking them first – hover over hyperlinks to see the web address and check any URL that seems suspicious.
- Even if an email seems urgent or threatening, never allow yourself to be pressured into entering personal data or sending it by email.
- In addition, you should always protect your device by keeping software up to date and installing a reputable antivirus program.
How do I know if my email address is being spoofed?
Unfortunately, it can be hard to know if someone is spoofing your email address – you may only find out if friends or business associates let you know they’ve received strange messages that seem to come from you.However, one sign of a spoofed email address is if your inbox is suddenly full of failed delivery notifications (AKA “bounce emails”) from the mailer daemon. If these are notifications from emails you did not send, they may come from emails that were sent out with your email address as the spoofed sender.
What should I do if my email address has been spoofed?
While strange bounce messages and reports of strange messages going to your contacts may be simply be signs of spoofing, they can also indicate a hacked email account. So, if your email address has been spoofed, take steps to strengthen your email security:- Check your account for unauthorized logins. mail.com customers can see account activity under: Settings > Manage Sessions
- Change your password. Make sure to choose a strong password and don’t reuse one from another account.
- Activate two-factor authentication. This keeps unauthorized persons out of your account even if your password is compromised
- Inform your contacts to be wary of any suspicious-seeming emails from your address.
How do I stop spoofing emails from my email address?
If you suspect that your email address has been spoofed, you should report the issue to your email provider. If you are not sure how, search for the name of your email provider plus the phrase “report abuse” to locate an address or form where you can report email spoofing. If you would like to report an issue to mail.com, you can contact our postmaster or our customer support.
While you can’t entirely prevent someone from spoofing your email address, choosing an email provider that uses SPF, DKIM, and SPF authentication can help act as a deterrent. Keeping your email address as private as possible also decreases the odds that a scammer will spoof it.
Good to know: The different meanings of spoofing
Often used to send phishing emails, spoofing is a cybersecurity risk that has become increasingly widespread in recent years. Generally speaking, however, spoofing simply means a person falsifying information so that they appear to be someone else. It is used by criminals to gain access to networks, devices, money, or personal data.
Spoofing can be used in many different sorts of scams, including:
Call spoofing: Caller ID spoofing, also known as call display spoofing, is when you receive a call from a phone number that seems trustworthy – often it’s the same number as the police or another government agency. The scammers’ goal is to try to get their victims to wire them money or reveal personal data for the purpose of accessing bank accounts or even identity theft.
IP spoofing: Also known as IP address spoofing, this sort of fraud operates on a machine-to-machine level. When data is sent over the internet network, the transmission protocol specifies that each information packet must have a header containing the IP address of the sender. In IP spoofing, the sender address is falsified so that it appears that the packet came from a trusted IP address. This form of spoofing can therefore be used to overcome network security measures.
SMS spoofing: This is when a scammer sends a fake text message to your mobile phone impersonating a trusted person or an organization. The text comes with a falsified sender name, phone number, or both – and like call spoofing, the aim is to defraud the individual who receives it. Unfortunately, SMS spoofing only requires basic computer skills; user-friendly SMS spoofing tools are widely available on the internet. In other cases, the scammers don’t even bother faking a phone number; instead, they impersonate a loved one, e.g., a child or grandchild asking for assistance.
Understanding how email spoofing works is the best way to recognize and avoid these potential threats to your personal and professional communications. We hope the information shared here empowers you to navigate your inbox more safely. We look forward to your feedback below!
This article first appeared on November 21, 2022, and was updated on January 16, 2025.
99 people found this article helpful.
Related articles